Using OSINT to track the proliferation of RCIED switches

Dave Ruddock, Chief Technology Officer looks at the proliferation of RCIED switches and how OSINT can be used to track them.
Dave Ruddock, Chief Technology Officer looks at the proliferation of RCIED switches and how OSINT can be used to track their use.
Over a socially distanced cup of coffee in our COVID-safe office, members of the EWS team were ruminating on the success and apparent proliferation of the AlphaFire firework remote as a preferred RCIED switch. Most made a reasonable attempt at guessing when it was first used but it was much more difficult to try and list the countries where it had been seen.
During a brief, brain-boosting chocolate biscuit pause, there then followed one of those age-old “What have let myself in for?” moments when one of the team (no-names, no pack-drill) piped in: Would it be possible to trace the usage and proliferation of the switch throughout the world? The gauntlet was thrown down.

AlphaFire remotes recovered at the arrest of a university scientist in Krakow, planning a Breivik inspired VBIED attack in November 2012
The truth is that without access to nationally sensitive exploitation data, it is a tall ask to track switch usage in this way, so I turned to our Open Source Threat Database (OSTD) to aid me in my search.
In most open-source descriptions, the make and models of switches are rarely given, so consequently we are heavily reliant on our experience and knowledge to identify component parts and items that have been photographed. This is a task that can be quite onerous when photographs have often been shrunk to fit the publishing medium, however we take a ‘human-in-the-loop’ approach to gathering OSINT over other datamining options to critically monitor information available in the public domain, which also allows us to ascertain overall trends and themes.

AlphaFire firework remotes in Barkhan District, Pakistan (August 2016)
Following the initiated VBIED in Oslo, Norway in July 2011 by Anders Breivik, his manifesto entitled “2083 – A European Declaration of Independence” was released on the Internet during his shooting spree on the island of Utoya which killed 69 people. The 1518-page manifesto was very comprehensive and included tactics, instructions for making explosives and recommended the AlphaFire firework 1Q remote as a moderately difficult RCIED trigger.
Interrogation of the OSTD showed that in the years following, there were several right-wing extremist arrests across Europe where the AlphaFire were recovered along with other extremist right-wing material, including in Poland and the Czech Republic. According to the OSTD events history, these were the first open-source recorded uses of the AlphaFire but since then their use has proliferated.
From the initial introduction of the AlphaFire in 2012, the technology has appeared in Israel (where various firework remotes are one the preferred switches) and in Pakistan in 2014.
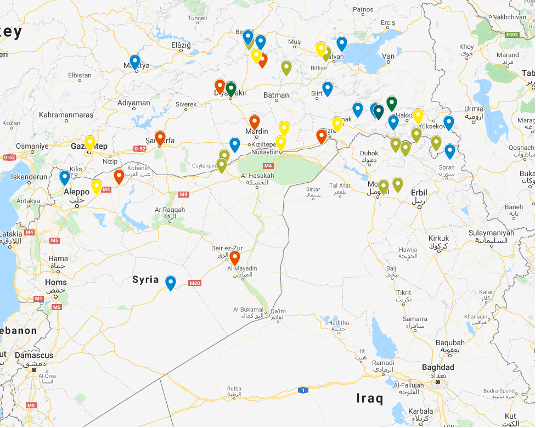
Use of the AlphaFire Firework Remote in Turkey, Iraq, and Syria over time
Since the Kurdistan Workers Party (PKK) first used the AlphaFire firework remotely in Sirnak Province, Turkey in 2015, it has steadily proliferated throughout various Turkish provinces over the ensuing years. When the Kurdish rebels crossed into Iraq and Syria, they took the technology with them and, as can be seen in map above, its usage has steadily grown becoming most prolific in Northern Iraq (Erbil) in 2020.
Naturally, it was easy to link the incidents in Poland and the Czech Republic to the Breivik manifesto, but it is difficult to prove the hypothesis that it was the genesis for the broader proliferation of this technology.
The OSINT in the OSTD allows us to see a clear Pakistan-Afghanistan connection, as is the Kurdish links to Iraq, Syria and Turkey, but it does not necessarily explain Italy and Israel.

Two complete boxes of 12 Alpha Fires with their associate remote controls recovered in a PKK arms cache in Sirnak, Turkey in October 2015




