How can ECM keep up with the evolving threat and can OSINT help?
Those of us who have been involved with electronic countermeasures (ECM/CREW/Jammers) for many decades have seen significant changes in the threat, the technology, and ECM availability, says Troy Phillips, Business Development Director at EWS. Once upon a time, ECM was only available to a small number of countries and specialist users and VIPs. That all changed around 2003 and billions of dollars have now been invested in the research and development and procurement of many systems and the evolution of a global ECM eco-system.
The Threat
Readers are very aware of the threat that the Radio Controlled IED poses and despite the availability of ECM, RCIEDs continue to increase globally. The graph right shows open source reports of confirmed RCIED attacks – there are many more that aren’t confirmed. (See: Confirmed RCIED Events 2015-2020 (Source: OSTD[1])
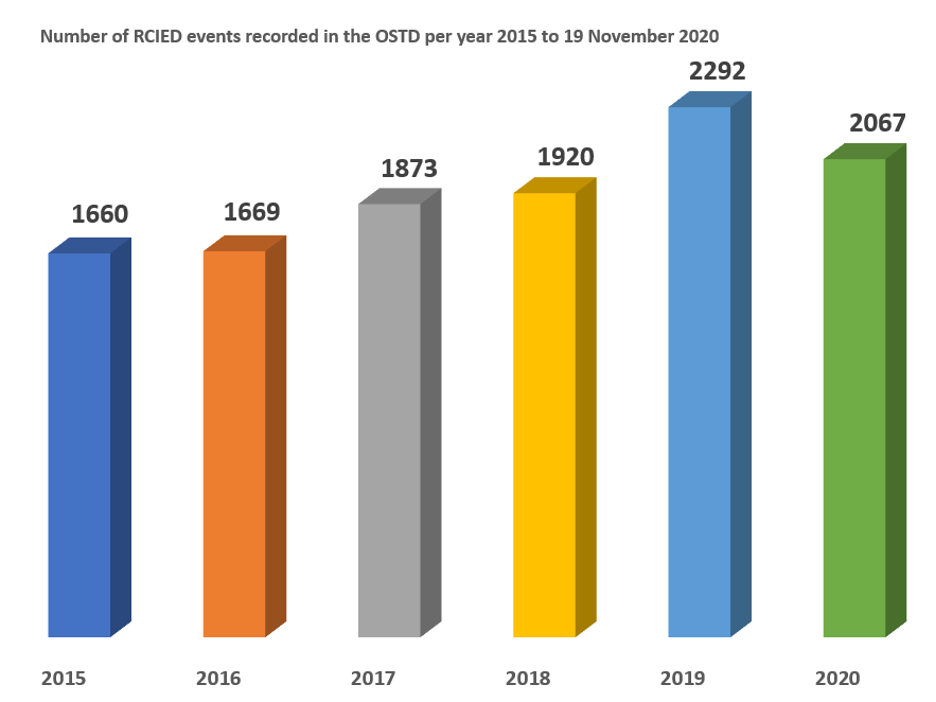
Confirmed RCIED Events 2015-2020 (Source: OSTD [1])
- Cell phones
- VHF/UHF Walkie Talkies
- Domestic appliance controllers
However, within these ‘top 3’ switches, there are many variations, and the commercial advancement of technology will have a natural impact on the type of switched deployed. For example, at present, perpetrators who use cell phones typically select the simpler, GSM type phones; smart phones are not seen often. There are many reasons for this, the most obvious being the cost and the simplicity of accessing sufficient current to initiate a detonator.
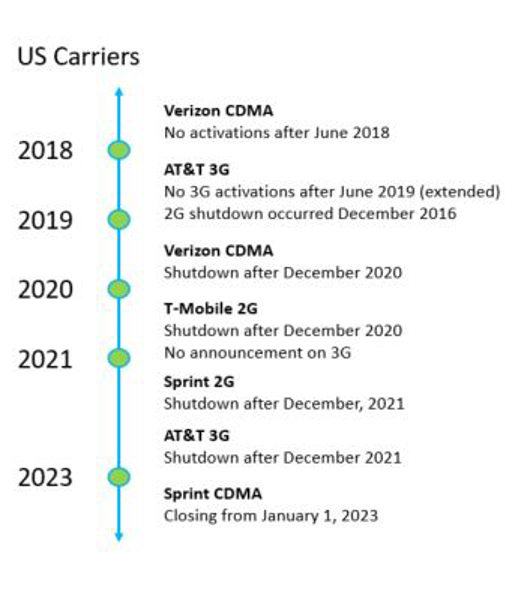
Current and planned closure of the 2G and 3G (CDMA) bands in the US (Source: Digi.com)
However, as we see 5G roll out globally, we are already seeing the demise of the 2G/GSM network. This will reduce the feasibility of using a GSM phone and therefore perpetrators will naturally migrate to smart phones or other switches. This will have an impact on IED switches and therefore ECM capability.

Example of LoRa device recovered in Burkina Faso, April 2020 [2]
Add to this the wide array of gadgets that continue to develop in the industry that is the Internet of Things (IoT), and you’ll appreciate that as an ECM specialist, defining the threat has never been more challenging. RF System on a Chip (RFSoC) technology continues to evolve, get smaller, have increasing functionality, wider spectral coverage, and of course is very inexpensive.
One factor that doesn’t change is the equation that Threat = Capability + Intent underpinned by Opportunity. All are factors we must consider when trying to mitigate the problem.
ECM
Whether we call our counter RCIED capability ECM, CREW, jammers, or electronic attack (EA), doctrine and terminology are organisational concerns. However, having effective ECM as we move into the 5G/IoT world continues to challenge even the sharpest minds in industry; 5G communications nodes will be everywhere resulting in self-healing autonomous networks. In the short to medium term we will see off the shelf communications moving higher up the RF spectrum and with the constant demand for new frequencies and increased bandwidth, the RF spectrum will be re-farmed and frequencies re-allocated.
Between 2003 and now, there have been huge advancements made in ECM technology – in particular the development of direct digital synthesis (DDS), FPGA technology, antennas, power amplifiers, and batteries. Massive changes have been made in the miniaturisation of the technology and the modularisation of systems. However, many (including the author) see that this technology, although still viable, is at the end of its developmental life.
There is, of course, another factor. ECM technology has quite rightly been very much focused on the asymmetric threat and non-state actor but it’s increasingly becoming a key technology used to match the near-peer adversary.

Armenian explosive laden s-UAS brought down by Azerbaijani EW assets, 23 October 2020 [3]
Military readers may well be familiar with the terms ‘Information Advantage’ and ‘Information Dominance’. Both terms are particularly important when addressing the near-peer or state-sponsored actor. There is probably no better example of what the current threat matrix looks like than the potential for an international flash-point in Nagorno-Karabakh [4] where the influence of Russia, Turkey (and therefore NATO), Iran, Israel, and Syria are all key players. In order to meet these complex operational challenges, the very latest generation of ECM has changed and will need to be flexible to meet the rapid advancement of technology in the next few years and beyond.
Cyber electromagnetic activities (CEMA) also play a key part of the armoury and will continue to support initially military deployed operations but will naturally evolve into the domestic ECM arena. CEMA recognises that cyber, electronic warfare (EW), and ECM must all combine in order to stand a chance of defeating certain actors/perpetrators and new tech.
At the start of the developmental path towards CEMA, ECM systems are, as a matter of course, using software defined radio (SDR) and increasingly adopt an ‘open architecture’ modularity. The aim of this open architecture is to move away from the ‘box’ concept; the idea being that systems are very flexible from both the spectral and protocol perspectives. This means that as threats evolve, hardware changes should be rare with only minor adjustments to ancillaries if needed – most changes will be simple software upgrades or the installation of new ‘apps’ to defeat new or emerging threats.
The Role of Open Source Intelligence (OSINT)
Publicly accessible information (PAI) when analysed into OSINT is one of the keys to the development and sustainment of current and future ECM/CEMA technology. Defeating the RCIED will always be a battle of tactics and technology from both the friendly and adversaries’ perspectives. Those who have known me for many years will have heard me speaking and delivering sermons on the importance of tactics and establishing exactly what perpetrators are doing and are likely to do in the future. I maintain that tactics are still the key to successfully defeating an RCIED – especially for those on the ground first, be they military, First Responders, and increasingly non-government organisations (NGOs) who are heavily engaged in clearing explosive remnants of war in areas of conflict.
What then can we do with OSINT? Firstly, we must understand that PAI has many pros and cons and we should measure how we use it and ultimately how we validate it before we analyse it into OSINT and turn it into something actionable. However, the amount of information available in the public domain is extreme but if you can find it, interpret it, and make informed decisions based upon it, it can be invaluable.
For example, 2020 was a challenging year from many perspectives, but the reality of the limitation of global travel has especially impacted those countering the IED. The many civilian entities who are ‘on the ground’ dealing with devices and feeding the exploitation machine have, in many areas, been withdrawn or have had their ability to freely move around curtailed. When there is war, exploitation is everywhere, but without this war-footing infrastructure and with the lack of movement due to COVID, exploitation becomes a real challenge. OSINT can help in many ways. Very often OSINT provides indicators and warnings in advance of the exploitation process and the production of other source (often classified) reports. Sifting through the information available is both challenging and key:
[5], EWS’s Intelligence Services Manager explains: “Today, The Internet has become a remarkable source of critical indicators and warnings for threatening behaviours. But OSINT derived from PAI isn’t just a case of running a few Google searches; to deliver actionable intelligence from which an informed response can be made, the challenge lies in knowing how to negotiate through the vast quantities of information on The Internet and social media. In effect picking out the particular needle of interest in a pile of needles. Our team maintains a 24/7 OSINT IED database that has over 40,000 events and we enter around 1000 new IED events per month from around the world. We sift our data into searchable categories using the UNMAS IED Lexicon [6] but even then, the amount of information can be overwhelming. We are actively looking at machine learning and artificial intelligence to assist with the challenge of making the most of our data.”
In order to meet the particular challenge of keeping ECM threat lists up to date and feeding the research and development needs of industry, we are constantly striving to find that key snippet of information that allows us to develop proactive planning in an industry that has been very reactive in the past. Those snippets of research can be widespread – from identifying a new device or finding tactical changes and intentions of adversaries, to the development of new communications systems and the roll out of new networks, etc. Being proactive and identifying what each of these snippets means to the operational user is key. Like elite athletes, the key to achieving success can be based on very small improvements across many areas that make up an ECM capability. Having a capability to horizon scan looking for any potential risk is essential and clearly OSINT is just one of the factors that contributes to this ongoing challenge.
Summary
As the variety and functional use of RF technology evolves, cellular networks change, and perpetrators still see the great tactical advantages of the RCIED, those of us in the ECM world will continue to be challenged, potentially like never before. In order to meet this challenge, the ‘ECM eco-system’ must evolve and strive to be proactive; we must follow the trends both tactical and technical and be prepared. As part of many sources of intelligence, OSINT has a key part to play in sustaining the ECM capability and keeping us ahead of the opposition, whatever that opposition looks like.
— — — — —
This article first appeared in The Detonator January / February 2021
About the Author
Troy Phillips has been involved in RF spectrum operations for almost 40 years. Initially as a British Army High Threat EOD ECM operator, Warrant Officer, and Electronic Warfare Operations Officer. During his second career in industry since 2005, Troy has been involved with many global counter terrorism related activities and in particular the defeat of the RCIED including the establishment of EW Solutions Ltd with his partners in 2009. Key achievements have been supporting such esteemed organisations as the FBI, the USMC, the UK MoD and UK counter terrorism policing, as well as many other entities globally. Troy is currently the ECM Advisor to the Executive Committee of the UK Industry’s Counter Explosive Ordnance group (C-EO UK) and concurrently is delivering a related Master’s Level course for Oklahoma State University. EWS continues to provide intelligence-led support to operations globally.
References:
[1] https://solutions-ew.com/intelligence-services/
[2] LoRa photo courtesy © les Forces de Défense et de Sécurité, Burkina Faso. The stock photo of the product next to it is ©Shenzhen Kelvin Electronics Company Limited.
[3] © Azərbaycan Müdafiə Nazirliyi (Azerbaijan Ministry of Defence)
[4] https://en.wikipedia.org/wiki/Nagorno-Karabakh_conflict
[5] EWS’ Intelligence Services Manager will be delivering an OSINT Masterclass as part of IABTI’s online webinars
[6] https://unmas.org/sites/default/files/unmas_ied_lexicon_0.pdf




